Engineering Radiation Tolerance: Design Strategies for Reliable Satellite and On-Terrain Defense Systems
VORAGO’s unique definition of Radiation-Tolerant performance definition – how chips are engineered, validated, and deployed.
By Parthiv Pandya, Director, Product Management
1. Designing for SpaceTech Reliability
Radiation tolerance is fast-becoming a foundational requirement across nearly every class of space orbit, air, and on-terrain mission—from CubeSats and tactical sensors to aviation and uncrewed ground vehicles (UGVs). Standard electronics stop at the edge of the map. Loitering Munitions must operate in "contested" zones—nuclear-adjacent sectors, high-EMI (Electromagnetic Interference) battlefields, and chemically hazardous areas, while Satellites are projected to grow from 14,000 today to ~50,000 by 2030 (https://www.voragotech.com/rad-tol-enables-autonomous-mobility).
The Problem: As autonomous vehicles and satellites scale, so does the threat landscape. Their systems’ decision-making core—the microcontroller (MCU) or microprocessor (MPU)—is vulnerable to radiation-induced soft errors (bit flips). With the largest solar flares in decades, we know the big damage that tiny electrical particles cause as we’ve seen in 2025 including the grounding of Airbus320 after it suddenly lost altitude and put several passengers in hospital.
The Gap: Military and commercial missions alike re currently forced to choose between "Overkill" (expensive space chips) or "Risk" (cheap automotive chips). They need a new partner who offers the right level of protection for the mission and at a far more affordable price.
Historically, teams viewed reliability as a binary choice between a radiation-hardened chip (high assurance, high cost) and a commercial-grade one (high performance, low assurance). Today, that dichotomy has evolved. Modern radiation-tolerant microcontroller combines commercial manufacturing methods with carefully engineered design features that suppress, detect, or recover from radiation-induced faults. Tolerance is not simply “less hardening”; it is a systematic approach that balances reliability, capability, and affordability.
The Rise of a Better Radiation Tolerance Category
In 2025, VORAGO announced an entirely new category of Radiation Tolerant by Design (RTBD) microcontrollers as the cousin to its traditional Radiation Hardened by Process (RHBP) MCUs. This article addresses what makes a chip “rad-tol” by VORAGO’s definition versus the weaker, riskier alternatives of up-screened commercial chips or triple mode redundancy (TMR) alone.
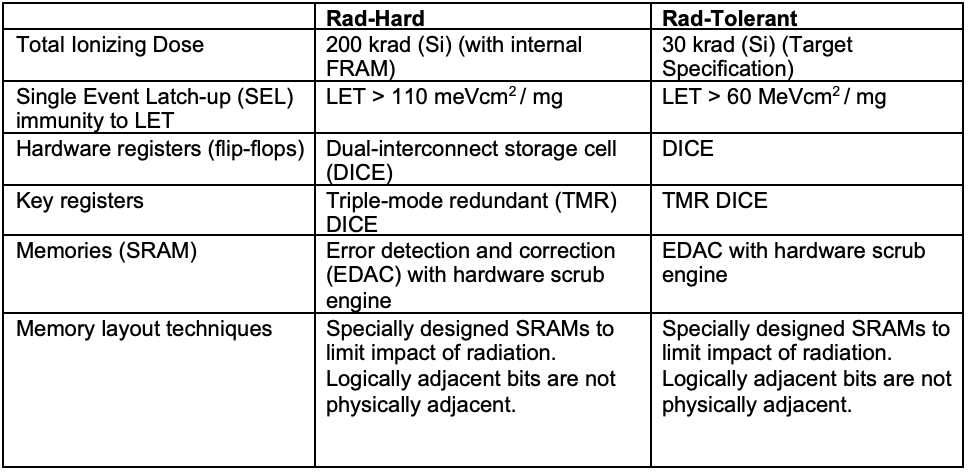
The following table shows differences and the similarities between the rad-hard and rad-tolerant devices. VORAGO’s rad-tolerant devices implement the same techniques to achieve better Single Event Upset (SEU) compared to the typical up-screened COTS part.
Radiation Performance Difference and Soft Error Rate Reduction Design Techniques
The key concept is resilience—designing robustness directly into the silicon, microarchitecture, packaging, and system-level firmware. This article provides an engineering-focused view into how that level of toughness – or radiation tolerance is achieved without HARDSIL®.
2. Understanding Radiation Effects
Radiation environments introduce both cumulative and instantaneous failure mechanisms. Engineers must understand these interactions before selecting or architecting a processor.
Total Ionizing Dose (TID)
TID effects are caused by accumulated charge in oxide layers, slowly degrading transistor threshold voltage, leakage, timing margins, and analog bias circuitry. Devices must maintain functional parameters beyond mission dose levels—often 30–100 krad(Si) for LEO missions and 200 – 300 krad(Si) for GEO or some deep space missions.
Single-Event Effects (SEE)
SEE mechanisms are driven by individual ion strikes generating charge in sensitive volumes.
Single-Event Upset (SEU): Bit flips in SRAM, registers, or configuration memory.
Single-Event Latchup (SEL): Parasitic thyristor activation causing runaway current.
Single-Event Transient (SET): Glitches on combinational logic that may propagate into state elements.
These effects arise at the device physics level but manifest at the system architecture level—making SEE mitigation a joint silicon–firmware–system challenge.
A Probabilistic Problem, Not a Binary One
Radiation tolerance is not “immune or not immune.” It is inherently probabilistic: the likelihood of failure depends on variables including cross-section, LET spectrum, device geometry, bias conditions, and system-level masking. The goal is not to eliminate SEEs but to control them within acceptable mission risk. This perspective underpins modern engineered rad-tolerant design.
3. Design-Level Mitigation Strategies
Radiation tolerance is not achieved through a single technique, but through defense-in-depth across multiple abstraction layers. Effective designs deliberately combine circuit-level hardening, physical layout controls, architectural fault containment, and firmware-driven recovery. Each layer mitigates one or more failure modes—SEU, SET, SEL, and cumulative TID effects—while controlling cost, power, and performance overhead.
Architectural Redundancy
Architectural redundancy remains one of the most effective and scalable mechanisms for suppressing SEE, particularly SEUs and SET-induced state corruption.
Triple Modular Redundancy (TMR)
TMR replicates logic or state elements three times and applies majority voting to mask a single fault. In radiation-tolerant processors, TMR is typically applied selectively, rather than globally, due to its significant area, power, and timing impact.
Most effective for control logic, configuration registers, and finite-state machines (FSMs) where a single upset could cause system-level failure.
Voting logic itself must be carefully designed to avoid becoming a single point of failure (e.g., hardened voters, temporal voting, or distributed voting).
Partial TMR is often combined with periodic state refresh to avoid latent multi-bit accumulation.
Fault-Tolerant Pipelines and State Machines
Rather than full replication, many processors implement fault containment at architectural boundaries:
Parity-encoded FSMs detect illegal state transitions caused by SEUs and force-controlled recovery paths.
Self-correcting counters and registers prevent monotonic drift caused by repeated upsets.
Pipeline stage isolation and replay mechanisms limit the propagation of transient faults before architectural commit.
Temporal filtering prevents short SETs from being latched as valid control signals.
These techniques allow designers to harden the most mission-critical logic paths while maintaining acceptable performance and power efficiency.
Layout-Based Protection
Physical layout plays a decisive role in SEE and SEL susceptibility—often more than logic design alone. Careful layout engineering can significantly reduce charge collection without requiring fully radiation-hardened processes.
Key techniques include:
Guard rings and deep well structures to intercept and sink charge generated by ion strikes, reducing parasitic bipolar activation.
Deep trench isolation (DTI) to electrically isolate sensitive devices and suppress lateral charge diffusion.
Increased spacing between sensitive nodes to minimize charge sharing and multi-node upsets (MNUs).
Current-limiting resistive elements around sensitive power domains to prevent latch-up from reaching destructive current levels.
Well-tie optimization and substrate contact density to improve charge evacuation paths.
These layout-centric approaches are especially valuable for engineered radiation-tolerant devices fabricated on commercial or modified commercial processes.
Component Selection
Engineered radiation tolerance at the system level begins with disciplined component selection. All active and passive components must be evaluated against the mission radiation profile, not just the processor.
Key considerations include:
Verified SEE cross-section data (SEU, SEL, SET) across relevant LET and energy ranges.
Documented TID limits, including parametric drift behavior—not just functional survival.
Proven lot-to-lot consistency and traceability.
Availability of radiation test reports or heritage in similar missions.
Firmware and Watchdog Systems
SEE mitigation is incomplete without firmware-level participation. Modern engineered radiation-tolerant systems assume that faults will occur and focus on detecting, isolating, and recovering from them deterministically.
Common firmware-assisted mitigation strategies include:
Independent watchdog timers to recover from processor lockups or control-flow corruption.
Health-monitoring firmware that tracks ECC error rates, clock integrity, voltage excursions, and thermal anomalies.
Memory scrubbing routines that periodically correct SEUs in SRAM and register files before multi-bit accumulation exceeds ECC capability.
Checkpointing and state restoration to allow graceful recovery after resets.
In many missions, firmware is the difference between a transient upset and a mission-ending fault. Systems designed without robust firmware mitigation typically require far more aggressive (and potentially expensive) hardware hardening.
4. Verification and Testing
Radiation tolerance must be quantified, not assumed. Quantification relies on a combination of modeling, simulation, and empirical testing to demonstrate predictable behavior under radiation stress.
Modeling and Simulation
Early-stage modeling enables engineers to identify vulnerabilities before silicon is frozen:
TCAD simulations model charge deposition, collection paths, and device-level sensitivity.
SEE strike modeling evaluates transient pulse widths, amplitudes, and propagation through logic.
Fault-injection simulation at RTL and architectural levels quantifies system-level impact of SEUs and SETs.
Mission-profile analysis correlates predicted upset rates with orbit, shielding, and duty cycle.
These tools allow targeted hardening, rather than brute-force over-design.
Radiation Hardness Assurance (RHA)
RHA provides the empirical foundation for qualification in aerospace and defense systems.
Typical RHA activities include:
Heavy ion testing to characterize SEU, SET, and SEL cross-sections across LET ranges.
Proton testing to capture displacement damage and proton-induced upsets.
Dose-rate testing for military and nuclear survivability requirements.
Lot acceptance and surveillance testing, ensuring production wafers meet the same radiation performance as qualification units.
Consistency and repeatability are critical. Technologies such as those used by VORAGO emphasize tight process control to maintain predictable SEL thresholds and TID behavior across manufacturing lots, an often-underappreciated requirement in long-lived programs.
5. System-Level Perspective
Engineered radiation tolerance is ultimately a system property, not only a silicon feature. Modern spacecraft and defense systems integrate device-level robustness with architectural redundancy and software-driven fault management.
Integration of Radiation-Tolerant Processors
When correctly integrated, a radiation-tolerant chip forms the backbone of a fault-tolerant system:
ECC-protected memories prevent silent data corruption and SEU accumulation.
SET filtering and clock synchronization prevent transient glitches from corrupting architectural state.
Power-domain segmentation limits SEL impact and enables selective reset or recovery.
Graceful degradation strategies maintain partial functionality under fault conditions.
The tougher chip becomes an enabler of system resilience rather than the sole line of defense.
Hybrid Architectural + Software Approach
Modern designs increasingly favor a hybrid approach:
Use radiation-tolerant processors for deterministic, safety-critical control functions.
Implement system-level redundancy (cold spares, voting, reset domains) to handle rare or extreme events.
Rely on firmware-based detection and recovery instead of excessive hardware hardening.
Meeting Mission Requirements Without Full Rad-Hard Cost
For LEO constellations, responsive space, and cost-sensitive aerospace programs, engineered radiation-tolerant solutions enable:
Faster design and refresh cycles
Reduced qualification and procurement friction
Lower hardware and integration cost
Reliability commensurate with mission risk, backed by SEE and TID characterization.
As a result, rad-hard versus rad-tolerant is no longer a binary decision. Many modern missions deliberately choose radiation tolerance as part of a system-level risk management strategy—allocating protection where it delivers the highest return.
6. Conclusion: Getting Tougher at Lower Radiation Levels
Radiation tolerance has matured into a disciplined engineering methodology. An engineered radiation-tolerant processor is not defined by what it lacks relative to rad-hard parts, but by how intelligently it integrates design-level and system-level protections.
Today, new RTBD chips can toughen low orbit spacecraft, aircraft, UGVs, and any equipment against up to 30 krad (sI) TID – and to make it cost-effective. The secret is co-designing and co-manufacturing rad-tolerant chips in parallel with their radiation-hardened counterparts. That means very VORAGO MPU and MPU will have radiation-harden and tolerant options over the next three years – starting with the VA4 family shipping in Q1 2026.
Engineers should evaluate devices based on verified performance—SEE cross-sections, TID curves, latch up margins, and recovery mechanisms—not merely by classification labels. As missions evolve, the industry is redefining reliability through smarter design, advanced process techniques, and architecture-driven resilience.
VORAGO’s long-standing work in high-reliability semiconductors demonstrates how commercial processes, when combined with engineered radiation tolerance, deliver robust and cost-effective solutions for space, satellite, and ground military and defense applications.